NY Fed feared cyber attacks before BB heist
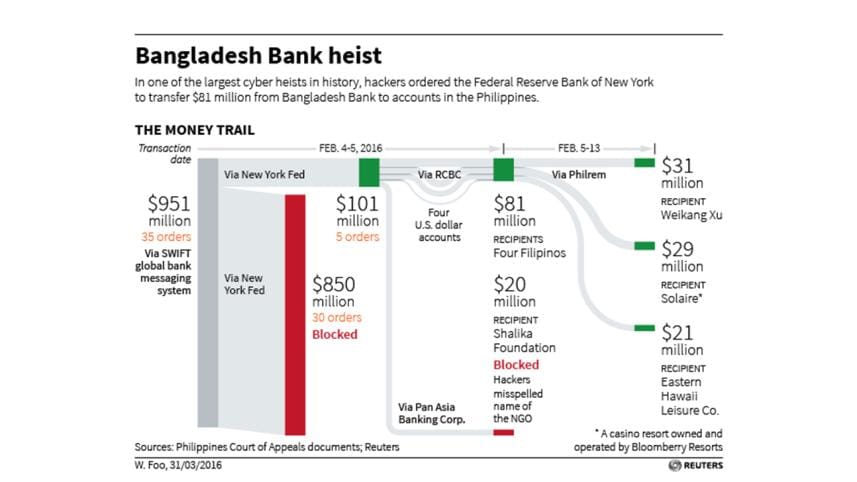
In the years before hackers stole $81 million from a Bangladesh central bank account at the Federal Reserve Bank of New York, senior Fed security officials examined the risk of such an attack - but judged the prospect unlikely, bank sources said.
The Fed managers worried that lax security procedures and outdated technology at some foreign central banks could allow cyber-criminals to commandeer local computers and breach foreign accounts at the US central bank, according to interviews with seven current and former New York Fed officials and a former US government official familiar with the discussions.
Over several years, New York Fed and Federal Bureau of Investigation officials discussed the risk of an attack made using the banking system's communications network, known as SWIFT, according to Fed and government officials, who spoke on condition of anonymity.
"The New York Fed was concerned with lots of vulnerabilities," said the former government official. "SWIFT was one of them."
But the Fed focused security resources on other priorities, such as preventing money-laundering and enforcing US economic sanctions, officials with knowledge of the bank's security operations told Reuters. Fed officials took some comfort in the fact that SWIFT's security software had never been cracked, the officials said.
The immediate result of the breach for the New York Fed is a claim from the Bangladesh Bank for payment of lost funds and a potential lawsuit. Beyond that, the heist showed that the U.S. central bank long understood a potentially systemic risk to a vital global finance network, but was unable or unwilling to address it.
The New York Fed declined to comment on past security priorities or on whether it had made changes since the heist. SWIFT declined to comment.
Before the heist, some New York Fed officials considered the threat of fraudulent transfers ordered through SWIFT a "fat tail risk" – a statistical term for events with low probability but dire consequences, said one well-placed official with knowledge of the discussions. February's theft from the Bangladesh Bank fit that definition - a bold cyber heist in which thieves attempted to withdraw nearly $1 billion in dozens of requests.
The crime rattled the banking industry because the conduit for the theft was the SWIFT network, an acronym for the Society for Worldwide Interbank Financial Telecommunication. A cooperative overseen by 20 of the world's largest central banks, SWIFT connects about 11,000 financial institutions globally that use it to order money transfers.
"What everyone is realizing right now is that no one has ever really appreciated the risk," said the person with direct knowledge of the New York Fed's deliberations.
SWIFT has said that the scheme involved altering SWIFT software on Bangladesh Bank computers to hide evidence of fraudulent transfers. Last week, SWIFT acknowledged that the Bangladesh Bank attack was not an isolated incident but one of a number of recent criminal schemes aimed at its messaging platform. SWIFT has declined to elaborate further.
Two Bangladesh Bank officials have told Reuters they believe both the New York Fed and SWIFT bear some responsibility for the failure to prevent the attack. The officials previously told Reuters that SWIFT gave Bangladesh Bank no prior warning about vulnerabilities, and the New York Fed failed to stop fraudulent orders when they reached New York.
The head of Bangladesh Bank is scheduled to meet next week with New York Fed president William Dudley and a senior executive from SWIFT to discuss the matter. SWIFT has said the attack was related to an internal operating issue at Bangladesh Bank, and the New York Fed has said it has no evidence that its systems were compromised.
Richard Dzina, head of the New York Fed's wholesale product office, in remarks at a banking conference Tuesday said bank workers "acted properly" in releasing the funds. The system was penetrated, he said, because the hackers had acquired valid credentials to order the transfers.
$80 BILLION A DAY
The New York Fed holds trillions of dollars in funds for central banks worldwide. It processes about $80 billion in fund transfers in and out of their accounts each day, according to a New York Fed official.
Security is handled by the New York Fed's Central Bank and International Account Services (CBIAS) division, a closely-guarded operation inside its fortress in lower Manhattan. CBIAS assigns risk profiles to individual countries and regions, assessing government stability, terrorism threats, and organized crime activity when deciding how to dispense cash to central banks and other official institutions, current and former Fed officials said.
In the months before the attack, the security unit was focused on bulking up its anti-money laundering protections, an initiative driven by the Board of Governors at the Fed's Washington, D.C. headquarters, according to two people familiar with the plan. Another priority was protecting the Fed's own Fedwire payments system from cyber attacks, several current and former Fed officials said.
Most transfer requests are approved automatically after computer screening. Only a few of about 2,000 daily transactions are flagged for review by employees, according to a New York Fed official.
One of the officials said automated scanners used for SWIFT payments were effective for preventing money laundering and enforcing economic sanctions - but would not defend the bank against fraudulent money transfers.
"There is a balance here that has to be struck between allowing customers to make new payments and to conduct their business in a timely manner, and also to prevent really obnoxious or obvious cases of fraud," said Shehriyar Antia, a former senior New York Fed policy advisor and analyst in the CBIAS unit.
The CBIAS system specifically checks for typographical errors - and it was a thief's typo, along with an unusually high number of requests for payments to private entities, that alerted the Fed to February's cyber attack, banking sources have told Reuters. Once alerted, the Fed suspended payments on most of the requests coming from the Bangladesh Bank, but not before the thieves extracted $81 million.
The Bangladesh Bank, Bangladesh police and the FBI are investigating the attack.
A Bangladesh police official who heads the department's forensic training institute previously told Reuters that SWIFT servers at Bangladesh's central bank were vulnerable to hackers because of the absence of a firewall and a lack of basic security protocols.
LOOSE CONTROLS
Three former officials said that the New York Fed had recently focused on loose controls over terminals and other access points to the SWIFT network at foreign central banks, where bankers often order withdrawals for hundreds of millions of dollars.
The concerns focused on the possibility that banks would purchase computers implanted with malicious software or that attackers could steal or buy legitimate credentials from employees, said the former U.S. government official. An additional worry, according to two former Fed officials, was the possibility that a corrupt insider — possibly a bank employee — might have access to the SWIFT network and submit a fraudulent payment request.
Years of managing foreign central bank accounts gave some Fed officials concern that certain banks were ill-equipped to handle local security because of a lack of infrastructure investment and other procedural problems. But the Fed does not have the ability to audit the security protocols at correspondent central banks.
"The vulnerability is that central banks, even in developing countries, have a lot of money relative to their level of sophistication," said the official with knowledge of the security concerns. "It's not just Bangladesh."



 For all latest news, follow The Daily Star's Google News channel.
For all latest news, follow The Daily Star's Google News channel.
Comments